When it comes to cybersecurity, malicious attackers will always discover the weakest point in a target’s defenses and focus their attacks on that area. As each area of cyber defense grows stronger, attackers move on to the next most vulnerable component. Operating systems, applications, and networks have been significantly hardened against threats in recent years. So, attackers are now looking at the least glamorous but potentially most-hazardous-if-attacked part of the security equation: firmware. Couple this with a continual increase in firmware threats over the last few years – and it’s clear that it is time to take firmware security seriously.
If a skillful attacker can compromise your device with malware at the firmware level, they can control the entire system above it… with almost no chance of detection.
Want to learn more about firmware and how you can improve your firmware security?
Download our eBook: Firmware is Foundational: Security in the Age of Edge Computing
The Basics
What is Firmware?
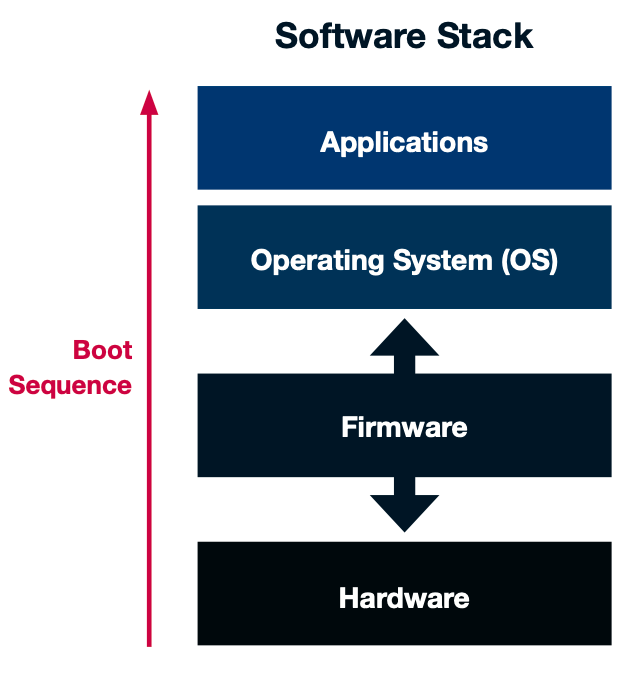
Firmware is software that’s responsible for the low-level control of an electronic device’s specific hardware. It consists of a set of instructions that tells the device how to communicate with other computer hardware.
Firmware can include basic functions that provide service to higher-level software or act as the device’s complete operating system (OS).
Firmware acts as a bridge that links the hardware and Operating System (OS) – critical for functionality, security, and flexibility.
Why Should I Care About Firmware Security?
The sad truth is that many manufacturers, from servers to medical devices, have treated firmware as a commodity part unworthy of high-level executive attention. While it’s true that few end users will ask questions about the firmware that controls the most basic plumbing in their devices, it’s that very obscurity that has made firmware such an appealing target. What’s more, since the firmware is the first piece of software executed when a device boots up, attackers can quickly escalate a successful firmware attack to own the entire device with little chance of detection.
Not only does firmware function below the normal range of threat detection solutions, but it also gives hackers a remarkable amount of systemic control. Once the firmware is hijacked, it can allow a wide range of tampering and eavesdropping. This, combined with general industry negligence in maintaining firmware security, should be of major concern for manufacturers of critical devices and platforms like computer and networking equipment, autonomous vehicles, medical devices, IoT devices, drones, automation robots, and more.
 This is no longer a theoretical threat. Firmware incidents and known vulnerabilities are increasing at an alarming rate. Companies must respond, but many don’t have the necessary in-house expertise. These companies should consider contracting with firmware security experts to provide the support services required to identify vulnerabilities and remediate them before and after manufacturing their products. Without this additional support, companies could be left facing firmware security issues resulting in attacks that cause:
This is no longer a theoretical threat. Firmware incidents and known vulnerabilities are increasing at an alarming rate. Companies must respond, but many don’t have the necessary in-house expertise. These companies should consider contracting with firmware security experts to provide the support services required to identify vulnerabilities and remediate them before and after manufacturing their products. Without this additional support, companies could be left facing firmware security issues resulting in attacks that cause:
- Corporate networking equipment can be compromised to give hackers access to a treasure trove of confidential information.
- Telecom or utility networks may stop working and put public safety at risk.
- Industrial IoT sensors can be hijacked with false readings, causing severe damage or injuries.
- Autonomous vehicles or medical devices in which a firmware hack can directly result in loss of life.
…Which can ultimately result in:
- Injuries and deaths
- Financial loss
- Regulatory penalties and fines
- Brand and reputational damage
Firmware threats are no longer theoretical. As more devices are connected to the internet of things, the risk of threats continues to increase exponentially. Organizations that don’t take the steps needed to improve firmware security could face devastating consequences.
The Problem: Firmware Security has Gaps
Since firmware is in every computing device, every device is exposed to threats. This inevitably means if you produce products with firmware, then you need to care about firmware security.
Firmware faces a broad spectrum of threats. For example, an attacker can exploit a memory buffer overflow to inject malware. Once the malware is installed, an attacker can easily elevate their level of privilege. This can also occur by injecting code at the System Management Mode (SMM) level of the firmware on Intel/AMD architecture. SMM is used to govern the most essential elements of a piece of hardware. Having access to this level of the firmware gives an attacker nearly universal systemic access and control—a privilege level higher than that of the OS Kernel or Hypervisors.
If an attacker gains control of SMM, they can do almost anything with the device and the software running on it. They can tamper with virtually any data on the device. With this level of access, hackers can take complete control of the device. They can exfiltrate sensitive data, steal or manipulate encryption keys, switch the device off, or even permanently break it like in the Saudi Aramco attack. SMM attacks are particularly challenging to mitigate because malware running in SMM has such high privileges that it is undetectable by Operating System anti-malware software. Some examples of firmware security issues include:
- Compromised flash memory
- Modified boot routines
- Heightened privilege advantage
- Supply chain vulnerabilities
The Solution: Firmware Security Risk Mitigation
Device and chip makers need to improve their firmware security to protect against threats. This requires developing a risk mitigation process that works across industry groups and internal resources.
Industry Groups
There are quite a few established industry groups that have already done a lot of the let work to help improve firmware security and mitigate risks. These groups work to develop and promote firmware standards and specifications that cover a range of different types of firmware security issues. These standards inform device and chip manufacturers how firmware should be built when it comes to the boot process. The leading organizations that support firmware security include:
- The Trusted Computing Group (TCG)
- Unified Extensible Firmware Interface Forum
- Distributed Management Task Force (DMTF)
- Platform Management Component Intercommunications Workgroup (PMCI)
- Fast IDentity Online (FIDO) Alliance
- Internet Engineering Task Force (IETF)
Industry groups provide a sound basis for developing an initial firmware security risk mitigation process.
Manufacturer Responsibility
While these industry organizations provide guidance for improving firmware security, it is still ultimately up to the original equipment manufacturers (OEMs) and original design manufacturers (ODMs) to ensure that these recommendations and protocols are actually implemented. This includes monitoring specifications and vulnerability alerts for anything that could impact the manufactured devices, as well as develop and distributing patches once notified of the vulnerability risk.
Here is where the biggest challenge lies: Many organizations don’t have the resources or expertise in-house to establish and implement these critical firmware security risk mitigation processes – even with the industry group support. So, what can be done?
While some OEMs are diligent about firmware patching, the reality is that many OEMs do not remediate firmware vulnerabilities.
Outsource Firmware Security Risk Mitigation to an Expert Partner
Instead of simply overlooking the need for patches, manufacturers can outsource their firmware risk mitigation to an established partner. Phoenix Technologies offers a solution with its subscription-based firmware mitigation service. By leveraging Phoenix’s expertise, organizations can begin remediating firmware vulnerabilities at a rapid pace to better protect themselves and end-users.
Phoenix Firmware Security Subscriptions
Phoenix offers a range of packages to help OEMs and ODMs improve their firmware security without hiring an in-house team of experts. Instead, Phoenix handles it all from tracking and notification of potential vulnerabilities to patch development and delivery. Phoenix has many deeply-rooted relationships in the firmware industry groups and major silicon vendors, making them the first to know when new firmware security threats emerge. They also maintain a comprehensive and detailed vulnerabilities database as well as sophisticated responses processes. The Phoenix FirmCareTM security-as-a-service program is an outsourced program for device manufacturers to leverage so they can be notified of the latest security gaps, receive patches, and successfully deploy them across devices.
Interested in learning more about our Phoenix FirmCare program?
Get the FirmCare eBook:
Phoenix Firmware Security Solutions
Phoenix also offers additional firmware security products and services to ensure that devices and firmware remain secure:
- Phoenix SecureWipeTM: Securely erases all data and partitions on Solid State Drives (SSDs) and Hard Disk Drives (HDDs) from the firmware, independent of the OS.
- Phoenix PassKeyTM: Combine firmware-enforced start-up protection with physical authentication devices, such as Smartphone/Bluetooth or FIDO devices, to provide resilient firmware-rooted anti-intrusion security for PCs.
- Phoenix BIOS Self-Healing: Automatically recover firmware from the last known backup with no user intervention when your system is in crisis.
- Phoenix Remote Management Console: Easily monitor, configure, and update firmware remotely from a single management console using the industry-standard Redfish framework.
Want more details on how to improve firmware security within your organization?
Download our eBook: Firmware is Foundational: Security in the Age of Edge Computing
Or if you’re interested in learning about what Phoenix can do for you…