Contact Sales: [email protected]

Phoenix Technologies provides efficient third-party penetration testing to identify and prioritize security risks, ensuring your product’s resilience against cyber threats and compliance with regulations. With over 40 years of experience, Phoenix provides comprehensive pen testing for a wide range of devices such as laptops, notebooks, tablets, servers (both standalone and cloud deployed), medical systems, IoT devices, home appliances, automotive systems and more. Phoenix also collaborates with security experts to stay informed about emerging threats and testing methodologies.
Phoenix has a well-defined, seven step process to maximize the effectiveness of a pen testing engagement.
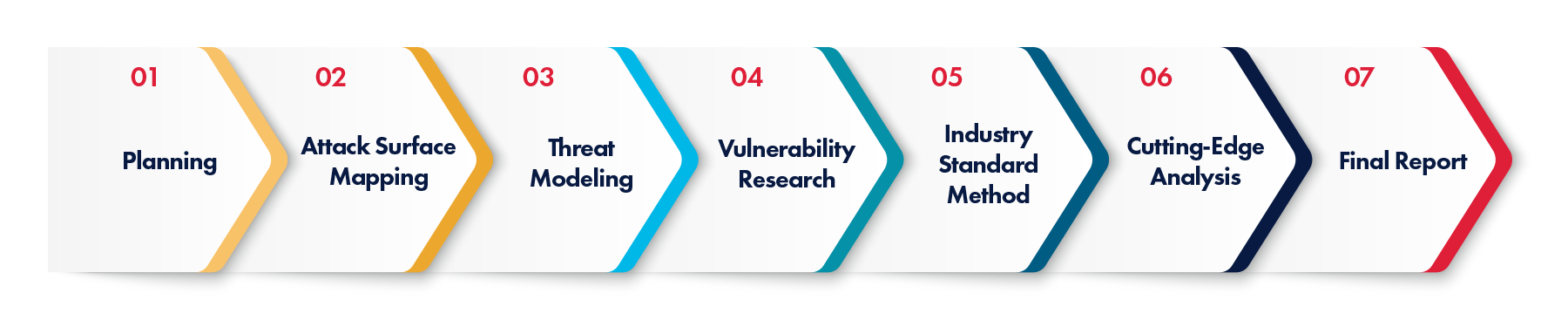
Following testing, a comprehensive final report documents findings, recommendations, and mitigation strategies. We prioritize discussing specific sections or recommendations with the customer, and our report includes a detailed vulnerability listing with severity ratings based on the widely adopted CVSS 3.1 scoring system for effective reporting and remediation planning.
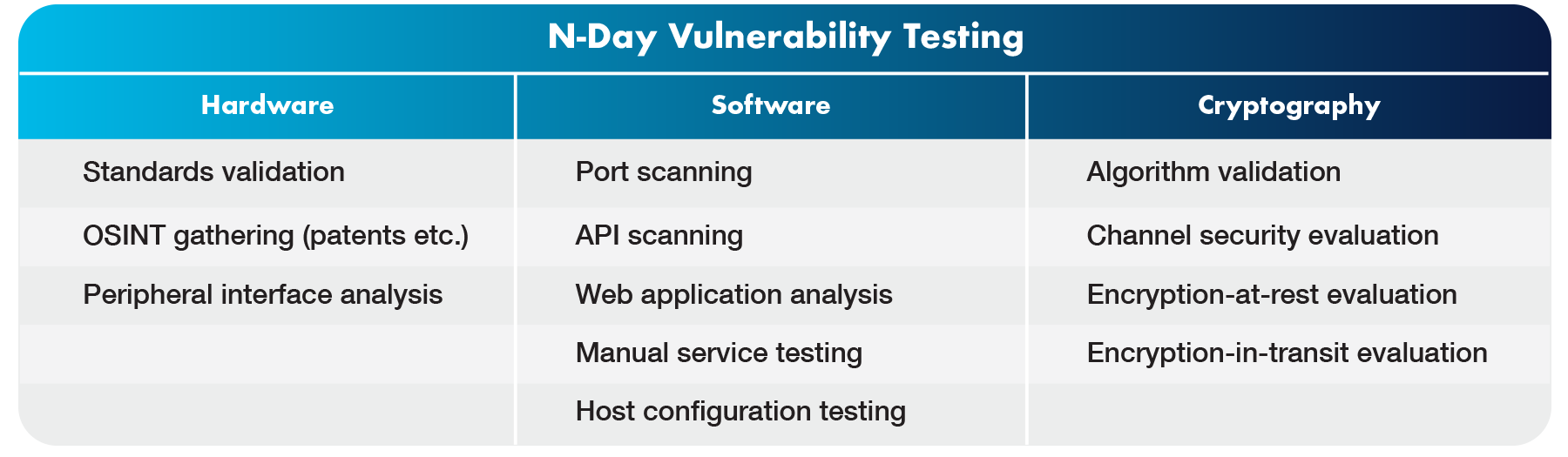
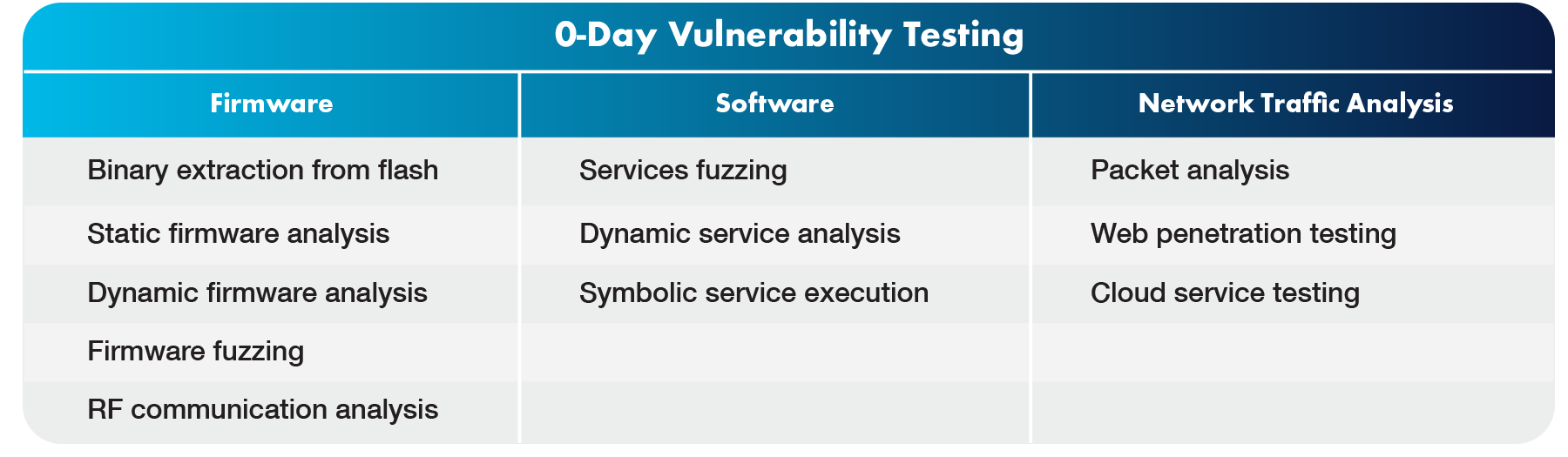
The specific actions taken to perform a penetration test on a product depend on the type of product being tested, the product’s security model, and the category of testing being performed. Some common actions Phoenix would perform for “n-day” and “0-day” vulnerabilities as part of a penetration test are shown in the following table.
Note: “N-day” vulnerabilities are those that are publicly known, possibly for significant periods of time. Many n-day vulnerabilities are trivial for attackers to exploit and their continued presence in actively shipping products can be embarrassing for a manufacturer.
Note: “0-day” vulnerabilities are novel and hence unknown to the public, but could be found and exploited by attackers at any time.
There are many categories of penetration testing performed by Phoenix, including threat modeling, on-device testing, long-term physical presence testing, short-term physical presence testing, and network-based testing. Threat modeling can be performed for any product, while the four other categories are specific to certain product types.

Phoenix has a dedicated security team to provide rapid response and resolution, along with security-focused code reviews and pen testing services. The team has well defined internal and external processes for processing disclosures and providing customers with security updates. In addition to original research, the Phoenix security team maintains a database of security reports from various sources including silicon vendors, independent researchers, government organizations, academic labs and UEFI related groups such as the USRT (UEFI Security Response Team). In fact, Phoenix chairs the USRT and holds the vice chairmanship of the UEFI SBOM (Software Bill of Materials) Team (USBT).
Phoenix Technologies has been authorized by the U.S. Department of Homeland Security (DHS) Cybersecurity and Infrastructure Security Agency (CISA) as a CVE (Common Vulnerabilities and Exposure) Numbering Authority (CNA). A CNA designation is only provided to well-known entities that have a history of demonstrated security credentials and capabilities.
As a CNA, Phoenix has the ability to directly assign CVE numbers to vulnerabilities discovered in its own source code, as well as vulnerabilities in third-party software discovered by the Phoenix security team that are not in another CNA’s scope. Phoenix can then publish that information via the CVE vulnerability list which feeds into the U.S. National Vulnerability Database (NVD) under NIST. Information technology and cybersecurity professionals around the world rely on the NVD to ensure they are discussing the same issue and to coordinate their efforts to prioritize and address vulnerabilities.
Company
Partners
Market Segments
Firmware Expertise
Products + Solutions
Services + Support
Legal
Copyright © 2025 Phoenix Technologies Inc. All rights reserved | Privacy Policy | Terms of Use | Cookie Policy | Trademarks
For any matters related to the domain phoenix.com, please contact [email protected]